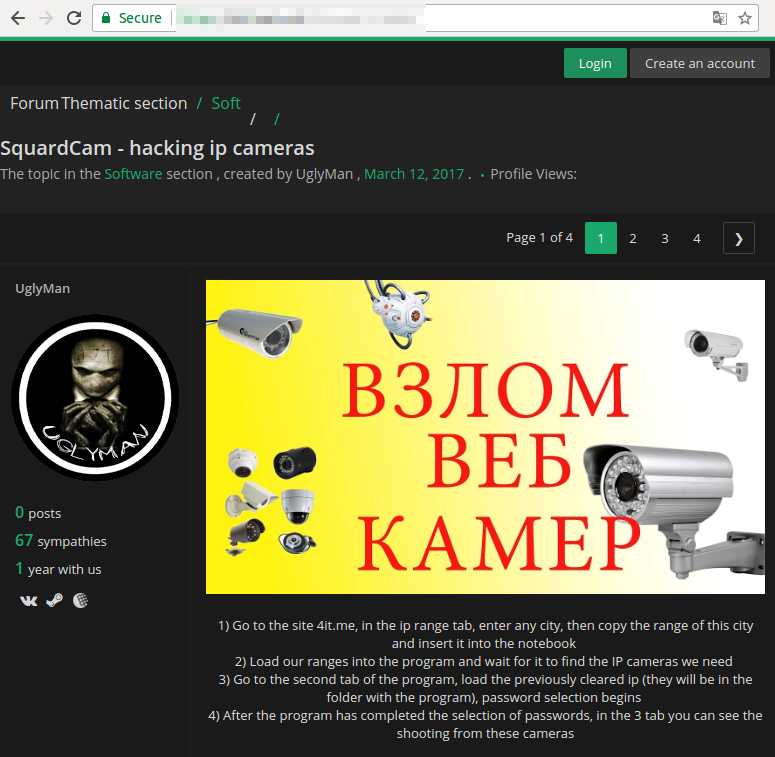
The Dark Side Of IP Cams: Hacked Feeds On Telegram – What You Need To Know
In an increasingly connected world, security cameras have become ubiquitous, offering peace of mind by allowing us to monitor our homes, businesses, and loved ones from afar. From sophisticated surveillance systems to simple baby monitors, these devices promise enhanced security and convenience. However, there's a disturbing underbelly to this technological advancement: the widespread hacking of these very cameras, with their private feeds often ending up on public platforms like Telegram. This article delves into the alarming trend of hacked IP cameras, how they are compromised, the grave dangers they pose, and crucial steps you can take to protect your privacy. 


What Exactly Are IP Cameras?
Before we dive into the dark side, let's clarify what we're talking about. **IP cameras, or internet protocol cameras, are digital video cameras that send and receive data over a computer network.** Unlike older analog CCTV systems, IP cameras connect directly to your network, often via Wi-Fi or Ethernet, allowing you to view their feeds remotely through an app or web browser. They are a cornerstone of modern security, enabling real-time monitoring and recording.The Alarming Trend: Hacked IP Cams on Telegram
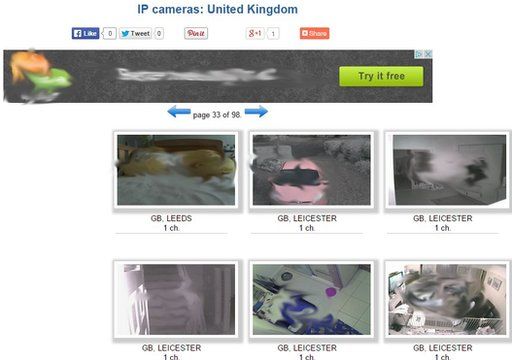
It's an unfortunate reality that **many cameras are being hacked now**. What's even more concerning is the ease with which these compromised feeds are shared and accessed. Telegram, a popular messaging app known for its channels and group features, has inadvertently become a hub for this illicit activity. **If you have Telegram, you can view and join hacked IP camera feeds right away.** There are numerous channels dedicated to sharing live streams from unsuspecting victims' homes, businesses, and even private spaces. Channels with names like **"Spy cam ip qr 📸" boast thousands of members, with one example showing 3.3k members**, openly sharing access to private cameras. Disturbingly, some channels delve into highly unethical and illegal content, with searches like "Ip cam incest mom son real search more" highlighting the extreme violations of privacy and potential for criminal activity facilitated by these hacks. Similarly, channels like "nhóm hack cam tình nhân" (Vietnamese for "hacked lover cam group") underscore the deeply personal and intrusive nature of these breaches. There's a strong indication that this illicit sharing isn't just a manual process. **"As we all know, many cameras are being hacked now after hacking, new users are added to the cameras,"** indicating a systematic approach. One prevailing theory suggests **"that this is done automatically with the help of bots."** These bots could be responsible for identifying vulnerable cameras, gaining access, and then automatically adding new "users" (i.e., the hackers or their audience) to view the feeds. Some even theorize that these bots might leverage sophisticated software to **"automatically upload video from IP camera to the Telegram messenger in case of detection of people in the frame,"** turning a security feature into a surveillance tool for malicious actors. The underlying tools for such automation often involve complex scripting and configuration management, hinting at the technical sophistication behind these operations.How Do These Cameras Get Hacked?
The methods used to compromise IP cameras are varied, but they often exploit common vulnerabilities and user oversights: * **Weak or Default Passwords:** This is the most common entry point. Many users fail to change the default passwords set by manufacturers, leaving their cameras wide open to anyone who knows these common credentials. * **Outdated Firmware:** Like any software, camera firmware needs regular updates to patch security flaws. Unpatched vulnerabilities can be easily exploited by hackers. * **P2P Protocol Exploits:** **"A lot of those Chinese IP camera and DVR are offering some kind of P2P protocol to allow easy remote connection from anywhere, without any need to setup NAT or VPN."** While convenient, these peer-to-peer connections can sometimes have security weaknesses that allow unauthorized access, bypassing traditional network defenses. * **Lack of Network Security:** A poorly secured Wi-Fi network or an open port on your router can provide an easy gateway for hackers to access any connected device, including your IP camera. * **Phishing and Malware:** In some cases, users might inadvertently download malware or fall victim to phishing scams that give hackers access to their network credentials.The Grave Dangers of Hacked IP Cameras
The implications of having your IP camera hacked extend far beyond a mere privacy breach. The dangers are profound and multifaceted: * **Egregious Privacy Invasion:** The most immediate threat is the complete loss of privacy. Imagine strangers watching you, your family, or your daily routines inside your most private spaces. This includes feeds from baby monitors, living rooms, and even bedrooms. * **Audio Eavesdropping:** Many IP cameras come equipped with microphones. **"In rare cases, if hackers gain unauthorized access to the microphone of your security camera to eavesdrop or transmit audio, you may notice some unfamiliar voices or conversations from the area monitored."** This means not only are they watching, but they could also be listening to private conversations, revealing sensitive information. * **Facilitating Criminal Activity:** Hackers can use these feeds to gather intelligence for burglaries, stalking, or other malicious acts. They can observe when a house is empty, identify valuables, or track the movements of residents. * **Blackmail and Extortion:** The captured footage, especially if it's sensitive or embarrassing, can be used for blackmail or extortion. * **Dissemination of Illegal Content:** As evidenced by some of the disturbing channel names mentioned, hacked camera feeds can be used to capture and distribute highly illegal and unethical content, contributing to a dark corner of the internet.Protecting Yourself: Essential Steps to Secure Your IP Camera
While the situation may seem grim, there are concrete steps you can take to significantly reduce the risk of your IP camera being compromised: 1. **Change Default Passwords Immediately:** This is the most critical step. Create a strong, unique password for your camera that combines uppercase and lowercase letters, numbers, and symbols. Do not use easily guessable information. 2. **Update Firmware Regularly:** Check your camera manufacturer's website for firmware updates. These updates often contain crucial security patches that close vulnerabilities. 3. **Disable Unused Features:** If your camera has features you don't use, disable them. For instance, **"Generally speaking, security cameras like IP cameras, baby monitors, or surveillance cameras should be silenced if you don't use the speaker."** Extend this principle to remote access, cloud recording, or P2P features if they are not essential for your use case. 4. **Secure Your Wi-Fi Network:** Use a strong, unique password for your Wi-Fi network and ensure it's encrypted with WPA2 or WPA3. Avoid public Wi-Fi for accessing your camera feeds. 5. **Enable Two-Factor Authentication (2FA):** If your camera's app or service offers 2FA, enable it. This adds an extra layer of security, requiring a second verification step (like a code from your phone) even if your password is compromised. 6. **Consider Camera Placement:** Be mindful of where you point your cameras. Avoid aiming them at highly private areas like bedrooms or bathrooms. 7. **Research Before Buying:** Choose reputable brands known for their security practices and regular updates. Read reviews and look for information on past security vulnerabilities. 8. **Isolate IoT Devices:** If possible, segment your smart home devices (IoT) onto a separate network or VLAN to limit potential damage if one device is compromised. The proliferation of hacked IP camera feeds on platforms like Telegram is a stark reminder of the constant battle for digital privacy in our hyper-connected world. While the convenience of these devices is undeniable, their security often hinges on the vigilance of the user. By understanding the risks and implementing robust security measures, you can significantly reduce the chances of your private life becoming public spectacle. In summary, IP cameras, while beneficial for security, are increasingly vulnerable to hacking, with their feeds often shared on platforms like Telegram. This phenomenon is fueled by weak passwords, outdated firmware, and P2P vulnerabilities, leading to severe privacy invasions, audio eavesdropping, and even facilitating criminal activities. Protecting yourself requires proactive steps such as changing default passwords, regular firmware updates, disabling unused features, and securing your home network.
The tech flaw that lets hackers control surveillance cameras - BBC News
Exposed Video Streams: How Hackers Abuse Surveillance Cameras | Trend
Breached webcam and baby monitor site flagged by watchdogs - BBC News